Hacking a website used to deliver Malware
Introduction
While analyzing a sample from this morning, I found out it uses a URL to download the second stage. While messing around with the url, I found a file upload vulnerability ( more precisely blunder). I used it to upload a php file to fetch the hashes of all the second stages there.
I- The File Upload vulnerability:
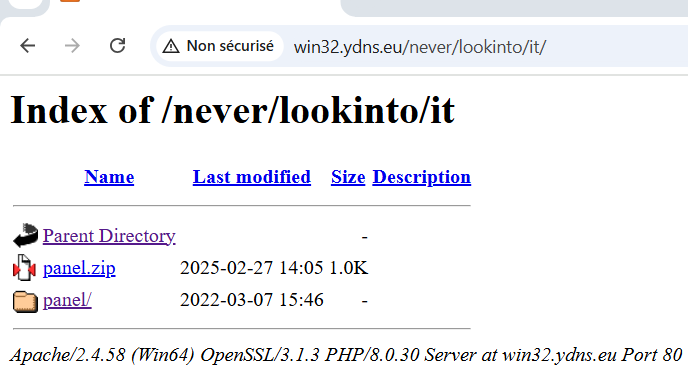
I always enumerate. When I found the URL from where the second stage is downloaded. I tried to find every path and see what happens there. I found this directory with a ZIP file
(1) Zip file in website
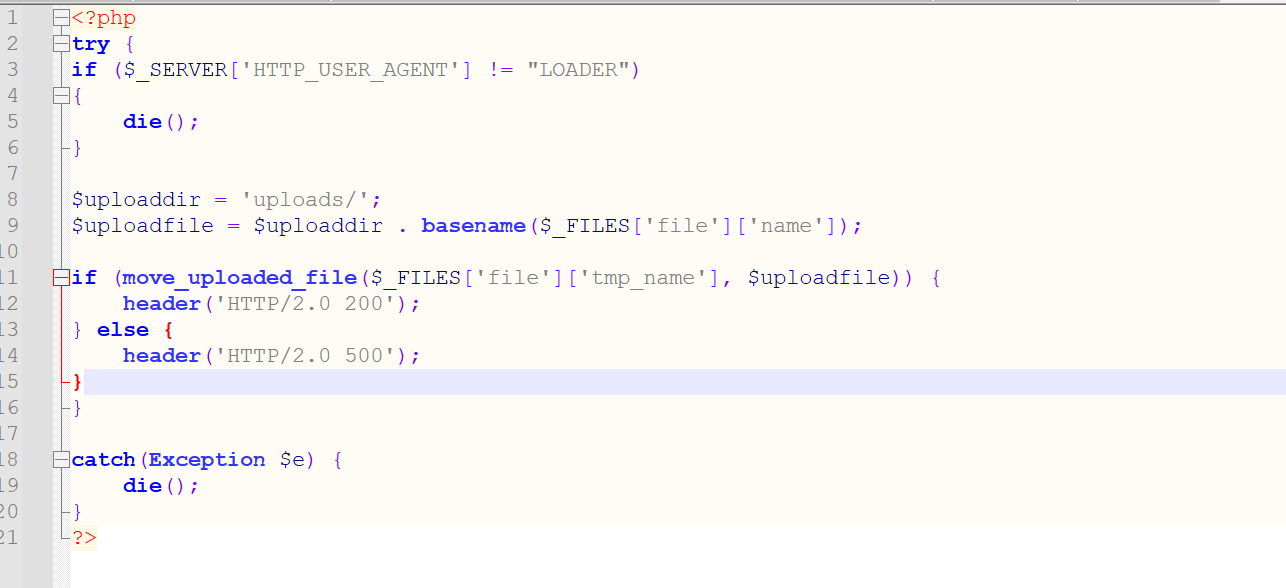
When you open the zip file, you see an upload.php file
It uploads files and only checks if the User-Agent is "LOADER".
Wrote a basic python script to upload files.
(3) Python script to upload a file to the website
II- Fetching the hashes of all the samples
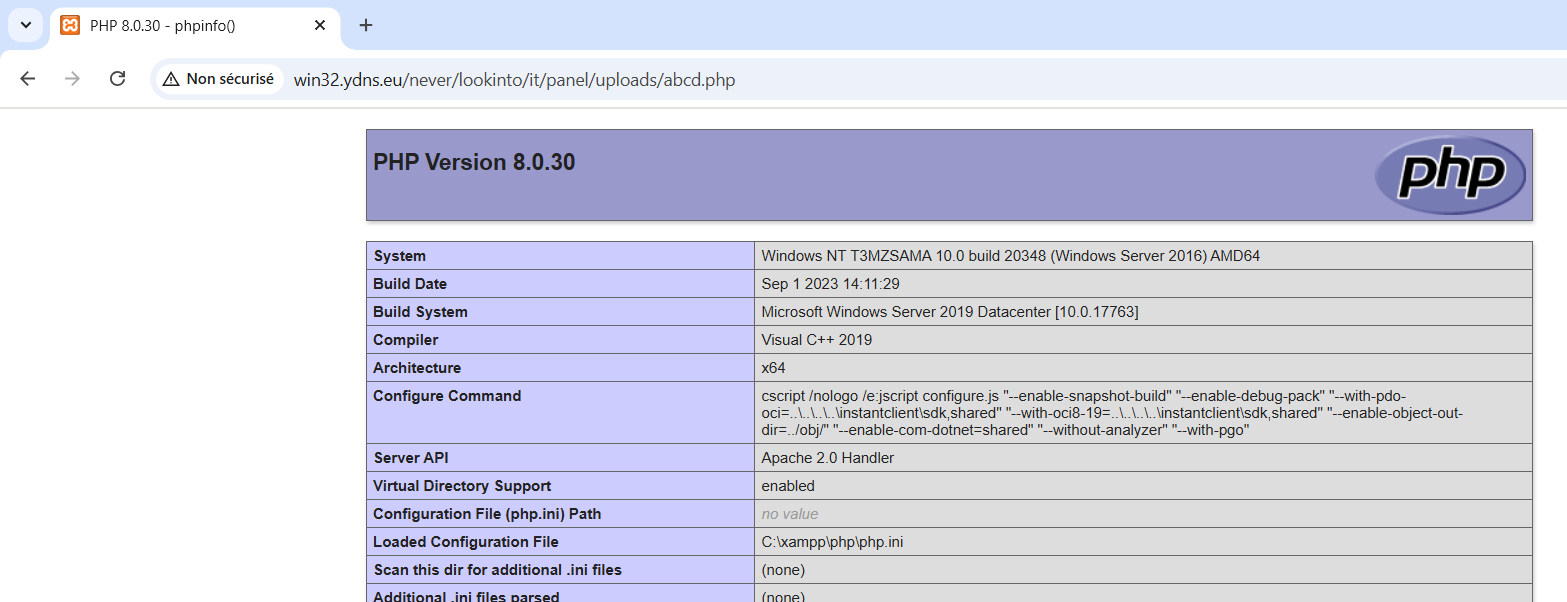
I tried uploading small php file containing only phpinfo() to check if the upload works.
(4) Phpinfo() works
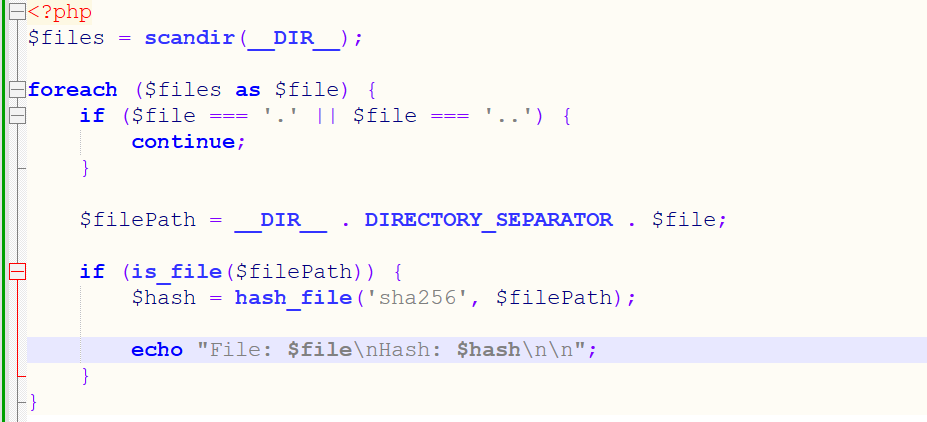
So, I wrote a PHP file to fetch all the hashes of all the sample on the website.
(5) PHP script to get the hashes of the files on the website
And it worked. We got the hashes of all the samples there.
(6) hashes of all the files on the websites
Hashes:
056df27e8ab520ada6f91d8734334f
0a921ec694bdd5d95d9643efa72a73
13652ca118b98ee7f713215094db92
1aecc3979eb3eee1e779e4eb652bcd
1b88197613f1c501120d3452c20a26
1b88197613f1c501120d3452c20a26
27b36145ae0389079a292b1189ff3c
304b156f8fce7e7aee41011fd7661d
444baa5f0e9d684d296e679e4ee7dd
4fe2a64ead98de53de5e7457b88824
53798111605041fa783c119fedf35b
590289bc95fc1253677f1b2c6e5333
5c62ac8e232df44816dc1cfff18ae9
61769cac0deb5d3a9c98e310152d98
650d95cc15334a3a0c8c06c4f80c2a
6c4a40ba44fe744debf7d3b37cb857
6fa55c058ce07658fd39dae990b270
71e02e244dc4e8ee6feaf8d2ea3cf9
741634e5b520fbc3fe99c4734618c6
783990d11819c473ccf153a73ac1ed
7d0923848648282a0804f1dffedddb
8a540451d8922eec3e75869b730468
8cba9355b5c5f36c22dd26170d46d4
8dd4c9cb7fe66bf2e7e5512d317c5f
8ed6f363fd129c095829065c2f3dc8
88025c2c5a48a9616e9662383483fe
b20ab05350ae824ec38d1da543ec8b
b2f558d08fecb7804d2699f7a0723a
b870c488a4946f65b8e0afad3307b2
b882d72547fbcbfc63e68faaf170ca
bf2e57d5710b78e19d1a43d72b9caf
bfebb7b8f30119d6d2081f299d2c12
c37060ac5111af141178e93bc84c8e
d14b7c95892867005647daae1a238a
d2f0924ef9051769f282edec31cad5
da45f4505a0b386489d1308b14474b
e500ec6e2d97a59e28feb5648c6da9
f8add5919847d7d9cffc255df0ec9a
f9ef24ea4de2798eb7591fdc0d6327
fd6fd560374f61b47a9a6184d3dbbe
0a921ec694bdd5d95d9643efa72a73
13652ca118b98ee7f713215094db92
1aecc3979eb3eee1e779e4eb652bcd
1b88197613f1c501120d3452c20a26
1b88197613f1c501120d3452c20a26
27b36145ae0389079a292b1189ff3c
304b156f8fce7e7aee41011fd7661d
444baa5f0e9d684d296e679e4ee7dd
4fe2a64ead98de53de5e7457b88824
53798111605041fa783c119fedf35b
590289bc95fc1253677f1b2c6e5333
5c62ac8e232df44816dc1cfff18ae9
61769cac0deb5d3a9c98e310152d98
650d95cc15334a3a0c8c06c4f80c2a
6c4a40ba44fe744debf7d3b37cb857
6fa55c058ce07658fd39dae990b270
71e02e244dc4e8ee6feaf8d2ea3cf9
741634e5b520fbc3fe99c4734618c6
783990d11819c473ccf153a73ac1ed
7d0923848648282a0804f1dffedddb
8a540451d8922eec3e75869b730468
8cba9355b5c5f36c22dd26170d46d4
8dd4c9cb7fe66bf2e7e5512d317c5f
8ed6f363fd129c095829065c2f3dc8
88025c2c5a48a9616e9662383483fe
b20ab05350ae824ec38d1da543ec8b
b2f558d08fecb7804d2699f7a0723a
b870c488a4946f65b8e0afad3307b2
b882d72547fbcbfc63e68faaf170ca
bf2e57d5710b78e19d1a43d72b9caf
bfebb7b8f30119d6d2081f299d2c12
c37060ac5111af141178e93bc84c8e
d14b7c95892867005647daae1a238a
d2f0924ef9051769f282edec31cad5
da45f4505a0b386489d1308b14474b
e500ec6e2d97a59e28feb5648c6da9
f8add5919847d7d9cffc255df0ec9a
f9ef24ea4de2798eb7591fdc0d6327
fd6fd560374f61b47a9a6184d3dbbe


Comments
Post a Comment