Gremlin Stealer: Strings decryption + Where data is uploaded
Introduction
This is a quick static analysis blog post. @solostalking shared with me on twitter a sample of a new stealer this morning. I decided to take a quick a look at it. Found how it decrypts the strings. It can be automated. I'll just showcase the algorithm.
sample: https://app.any.run/tasks/69325fa1-b37e-41dc-a1f8-bb0038345a3d
Decrypting the strings
Since it's a .NET sample. Let's open it in DnSpy.
Skimming through the methods of the main module, I found this one
Obviously, seeing a loaded resource and some obfuscation + it returns a string, you think it's a string decryption method.
It loads an encrypted resource. Uses the first and second parameters to calculate an offset. And finally a decryption routine.
Notice how all the elements of the array are xored with the SAME INTEGER which is the third parameter.
We can make use of Cyberchef's XOR bruteforce and bulk decrypt everything in resource.
We can recognize some strings such as chrome.exe etc...
But the result is very big to be skimmed through.
I'll save it to a file and look for thing like "http" and ".com" etc...
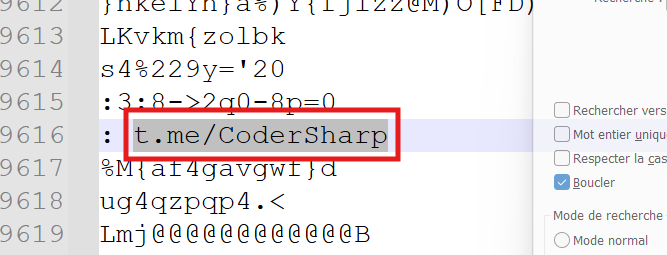
A telegram link
It most likely belongs to the author of the malware
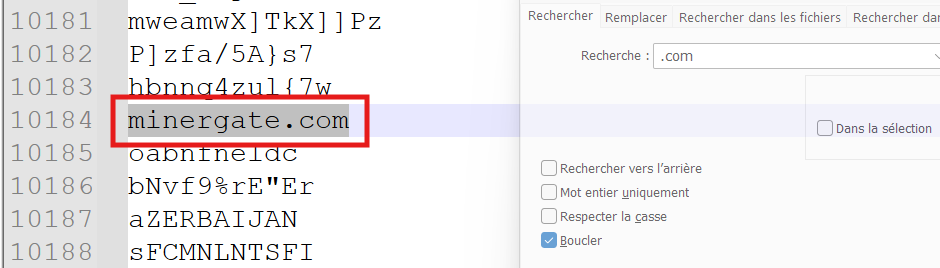
Searching for occurences of the string ".com" gives us many domains
minergate.com is a mining pool. So, it's very likeley that the malware implements mining functionalities.
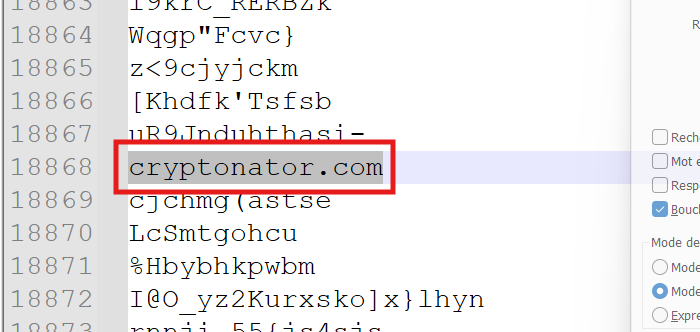
You also find several other domain related to blockchain including cryptonator.com .
Which was seized by the autorities
You can call it the Lumma effect, but whenever I find a steam profile in a sample I suppose it's using it for Fallback C2's .
Where data is uploaded ?
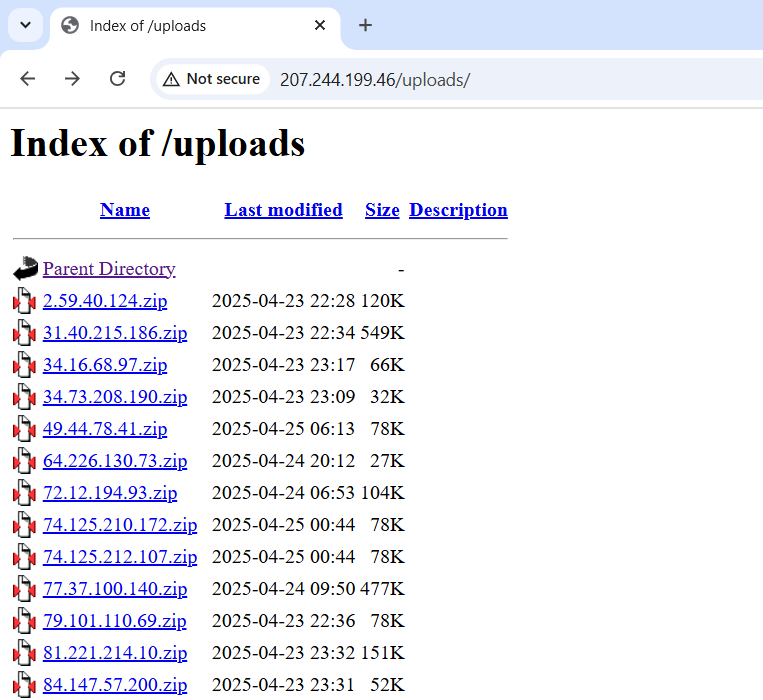
Once I found the C2 Panel http://207.244.199.46/ , I went and fuzzed its files and directories. And found the /uploads directory .
Second opsec failure after the XOR blunder ?
Conclusion
Obviously, more work needs to be done to check whether there are other C2's and to find the full steam profile link and other stuff. I wanted to share these findings, maybe it could help someone








Comments
Post a Comment