Another example of an Opsec failure in malware C2 Panels
Introduction
This is not going to be a long article. I wrote some article before about blunders in malware infrastractures. Some threat actors make some bad mistakes and that could cost them their infrastructures or logs in case of stealers.
- This article shows an example of a simple bug that could cost the threat actors their entire infrastructure https://www.rootkall.com/2025/03/hacking-website-used-to-deliver-malware.html
- This one is about a Stealer called Gremlin, the logs were accessible via an "Index Of" page :p https://www.rootkall.com/2025/04/gremlin-stealer-strings-decryption.html
I wasn't really sure if I should write about this case but sharing knowledge is always good.
As you can see in the screenshot, someone shared a C2 panel, and I love these in the sense that I try to compromise them. I pointed out in an answer to the tweet the blunder error that is made.
The C2 Panel is Open source:
A quick search of "C2WebServer" in a search engine would yield you the github repository of the malware as well as the Web Panel.
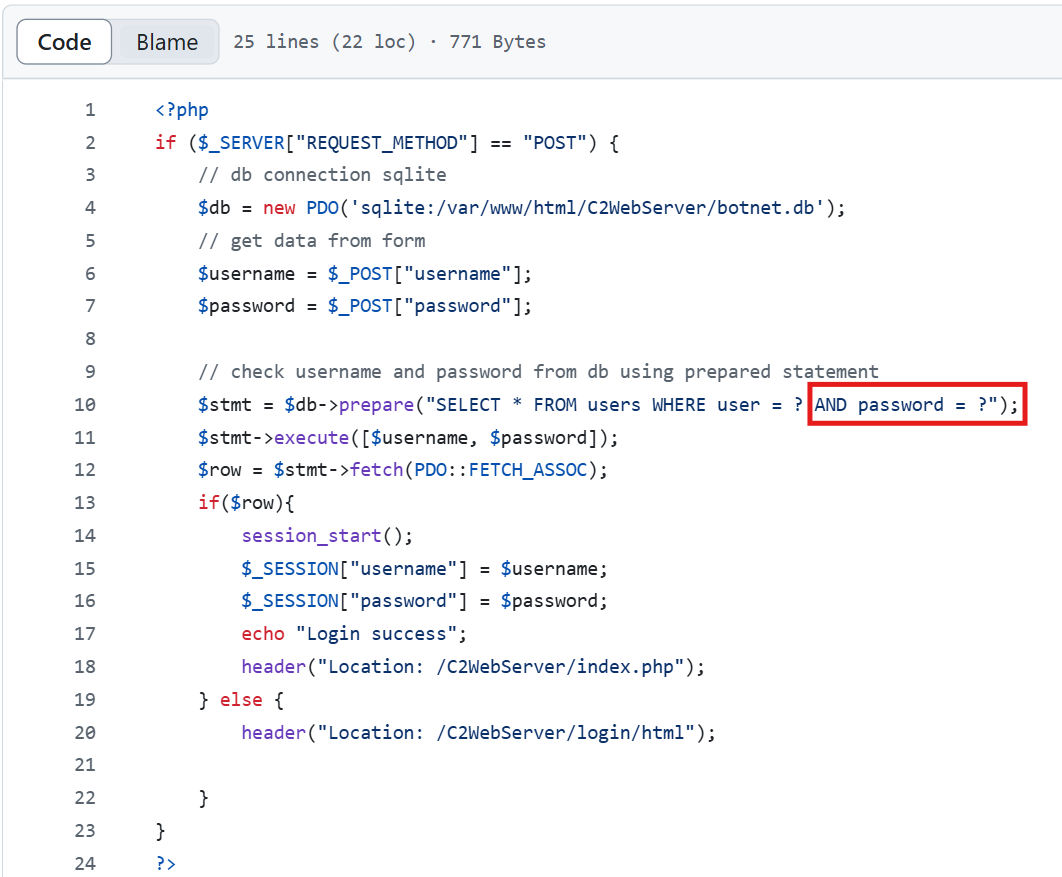
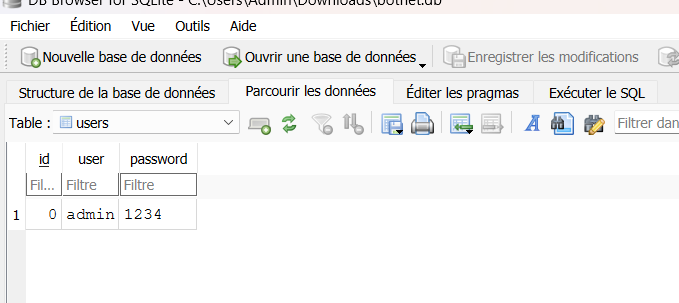
Taking a look at the "login.php" code shows something very weird. Passwords are not hashed in the database :p
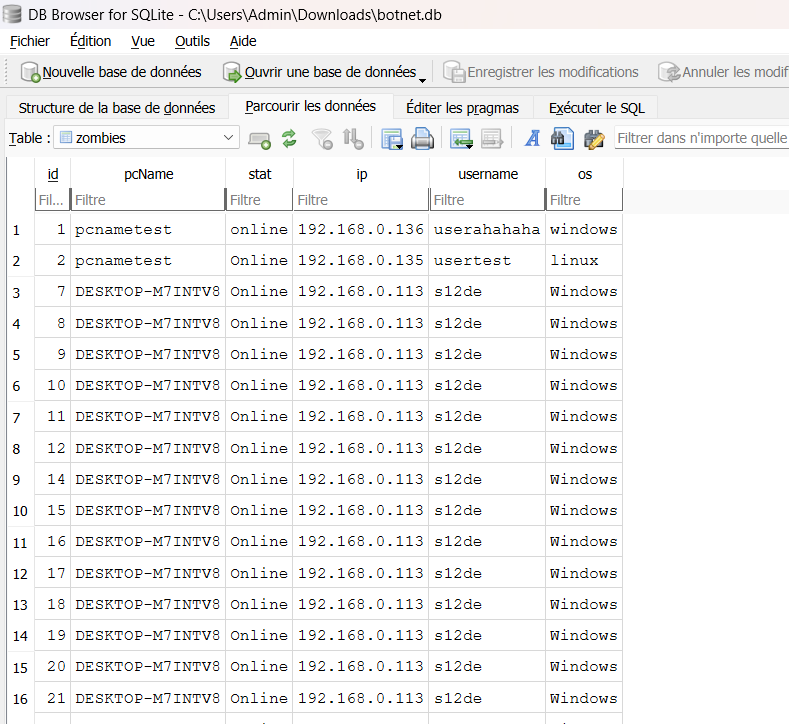
We can download it and read it DB Browser for example. We now have access to many interesting things.
Conclusion
Even though, this doesn't seem like a serious campaign. It does highlight the almost certain fact that every C2 Panel has a vulnerability and sometimes these are not really that complicated. I was not sure about writing this article but it seems like a good thing to share with people.




This comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
DeleteThis comment has been removed by a blog administrator.
ReplyDelete